Security covers many dimensions, including the physical and logical. As such many employees, including executives, do not or choose not to understand its implications well. Instead they seem to prefer to leave it as a speciality which only the security specialists have to deal with, and which they can therefore sublimate. This is not a positive way forwards. A, necessarily anonymous, example demonstrates what can happen, albeit unintentionally.
An international organisation, with offices around the world with a mix of local and head office staff, sends out senior managers to lead from the front. Each office possesses both commercially confidential and sensitive internal information, on paper and in local systems as well as via connections to main IT systems. In such circumstances there is a multi-layer need to ensure security.
Observed in a real world environment the reality on the ground demonstrated how organisations can lose focus on security. To give just one simple example, external utility staff were permitted unsupervised access to areas where access to systems and/or information was possible.
What was the problem? It was not that the managers were, de facto, incompetent. Rather it was that they had neither an understanding of the main principles of security (and the implications of failure), nor were they assigned responsibility and accountability, nor did they know how to recognise incipient problems and when to seek specialist assistance. Compounding this, management staff rotated: one consequence of this was that the chances of setting good security practices and policies were gently diluted over time, to the point that security became a word rather than something practiced constantly by all levels of employee.
If this example seems improbable, consider Figure 1, drawn from the recent Freeform Dynamics report entitled “The End User Security Jigsaw” .
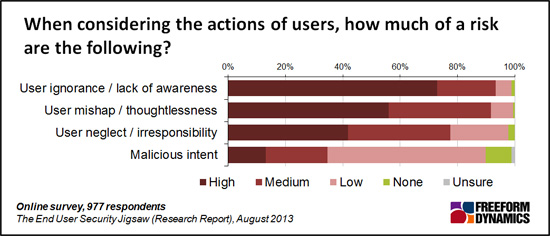
Figure 1
There are two significant issues here. The first is that malicious intent by users is important, but not the most important matter. User ignorance, thoughtlessness and neglect are of far greater significance, at least as viewed by the nearly 1000 respondents. Ignorance, thoughtlessness and neglect applied to the example above describe pretty accurately the state of those international offices. No-one was deliberately setting out to undermine security nor how security was implemented. But the cumulative effect was to deliver a level of security that was insufficient.
Why should this occur? From most viewpoints it is a fact of life that it is easy to pay lip service to the importance of security without needing to do much about it. Unfortunately security is a largely abstract concept, one that is all too intangible. This makes it that much harder to deliver a suitable level of awareness. Yes, you can make it exciting by telling all the war-stories of who did what to whom – but most of these instances are largely irrelevant to the necessary procedures that are needed for day-to-day security. The difficulty is that decent security is about good procedures and practices delivered daily. You know you have to brush your teeth each day, to avoid the dentist: the price of not doing this is personal pain (and the cost of the dentist). Failing to deliver security does not have quite the same obvious pain points for the individuals who must ensure it happens – unless responsibility and accountability are made part of each employee’s job, including those of executives who should be leading by example.
The key to practical security lies, therefore, not just in having a ‘security programme’ in place. It is also necessary to provide a blend of relevant, regular technology awareness and education that are delivered in the right way – focusing on the few aspects that really matter to each level of employee. Perhaps counter-intuitively, do not ask people to do too much but do associate security with clear lines of responsibility and accountability.
This does not mean that every senior manager, manager or even employee has to become a security expert. Far from it. Indeed, organisations should avoid most employees trying to become security experts. Instead, they should know enough to understand when to ask for expert assistance.
There is nothing profound in this. In fact it happens daily in other areas of life. You smell burning so you turn off the stove or the electricity supply and send for the electrician or the firemen: you do not, unless you are certain of what you are doing, try to fix the problem yourself.
In turn this suggests that security must also have a basis that is reflected in HR. For example, employees should have explicitly to sign off on a regular basis that they are observing whatever security procedures are applicable to them. This needs backing up with both rewards and penalties: rewards (whether monetary or other) when employees satisfy relevant standards and explicit penalties for those who fail. The latter should go as far as making sure that unambiguous HR policies exist which make it clear that certain behaviours represent disciplinary offences which provide justification for dismissal.
For some organisations, as Figure 2 shows, this already occurs. The ‘Confidant Group’ have an emphasis on proactive investment in, in this case in IT security. The ‘Others’ show significantly less involvement.
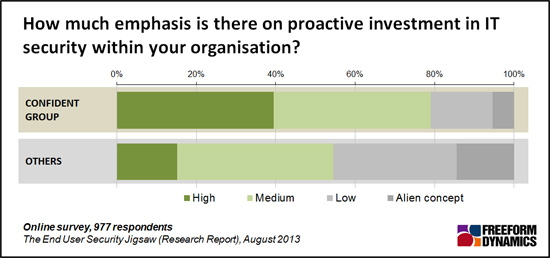
Figure 2
The important aspect to remember is that even with proactive investment it must be of the right form. It must not be just about technology or IT; for example physical security awareness – e.g. the need for supervising external utility or other visitors – also matters. Employees must be provided with the appropriate level of understanding so that they can protect an organisation’s assets and recognise when to seek help. This must be backed by HR policies which make clear who has responsibility for what, and how accountability is delivered. Finally, executives must be part of the whole, in order to lead by example.
Security education is a cost. Many organisations prefer not to invest in it, or cut this early when economic times are hard. Many are never affected by a security breach. But those that are can find the overall costs much greater than the immediate loss of (say) information – especially when compliance and regulatory authorities impose penalties. Put together security education should underpin all parts of the security jigsaw, as shown in Figure 3.
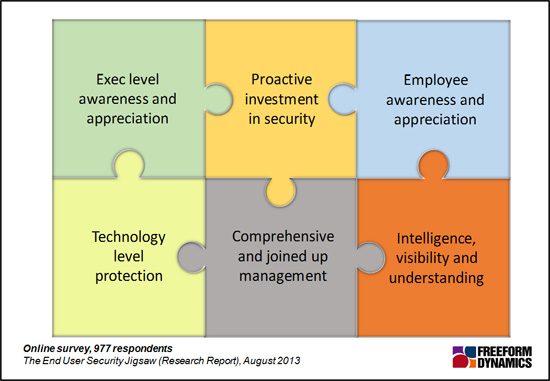
Figure 3
CLICK HERE TO VIEW ORIGINAL PUBLISHED ON

Content Contributors: Charles Brett
Through our research and insights, we help bridge the gap between technology buyers and sellers.





Have You Read This?
From Barcode Scanning to Smart Data Capture
Beyond the Barcode: Smart Data Capture
The Evolving Role of Converged Infrastructure in Modern IT
Evaluating the Potential of Hyper-Converged Storage
Kubernetes as an enterprise multi-cloud enabler
A CX perspective on the Contact Centre
Automation of SAP Master Data Management
Tackling the software skills crunch