By Tony Lock
Bring your own device (BYOD) continues to attract considerable attention, but the proliferation of machines now being used in businesses large and small is exacerbating the problem of data fragmentation to a degree that is becoming hard to ignore. The routine usage of home computers, personal smartphones and tablets in everyday business life is creating data management and security challenges for organisations with which the channel can help.
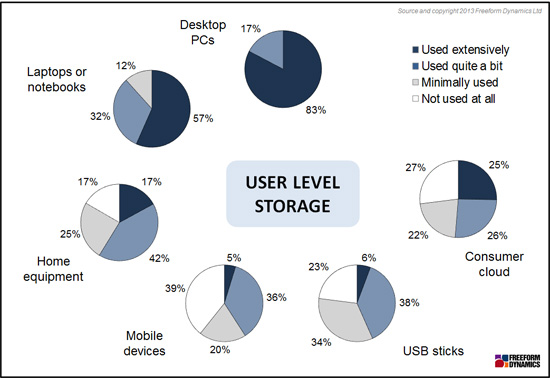
Figure 1
A recent online survey by Freeform Dynamics details the vast range of IT equipment that now holds company data (Figure 1). As might be expected, a majority of survey respondents reported that in addition to company supplied desktops and laptops home PCs are utilised to hold corporate data, even if only for short periods of time. But it is the fact that significant numbers already recognise that mobile devices and ‘consumer cloud’ services are either being used, or are at least suspected of being utilised, that illustrates the breadth of the challenge IT now faces when it comes to ensuring corporate information is being managed securely and cost-effectively.
When questioned explicitly concerning issues arising from data fragmentation, a number of pain points are revealed.
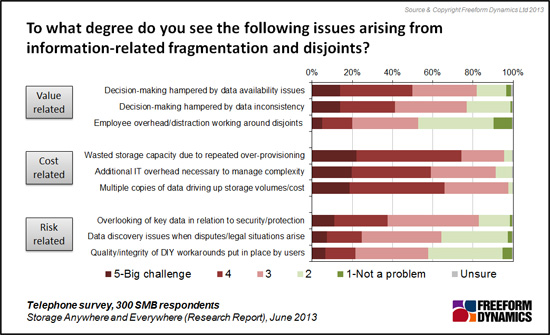
Figure 2
As is evident in Figure 2, many IT professionals are very concerned by the risks posed by the impact of data fragmentation on their business. Various “security” related issues are highlighted as you might expect, though it’s telling that the decision making and employee productivity impacts are seen to be at least as important. This reflects other research we have carried out hat shows a majority of businesses believe that they do not exploit the data they hold as effectively as they could.
But the factors that are most widely seen as significant challenges are related directly to the cost of storing and managing rapidly growing volumes of data spread across an expanding range of systems. This includes both those directly administered by IT and those often outside of its central management.
Despite the challenges and concerns, very few respondents say they have adequate policies or procedures in place used to control where corporate data is stored.
Taken together there are multiple opportunities for channel organisations to help customers. And many of the areas of greatest promise can be deduced from looking at the responses of an “elite” group of those taking the survey. This group was composed of those found to be most effective at managing and exploiting information and managing information-related risks effectively.
When compared with other respondents the elite subset identified a few key steps to help minimise the costs and risks arising from data fragmentation. Each of these steps is well suited to channel engagement via the delivery of relevant solutions and services.
Top of the best practices identified is simply to identify where different “categories” of data are stored. The discovery and classification of data are tasks well suited to modem storage/ asset management tools combined with good practice. But bear in mind that it is rarely productive to try and boil the ocean at once. Instead proceed step by step so that the customer can see benefits quickly.
The next steps are then likely to focus on ensuring that the customer puts in place policies that cover where, on internal systems, privately owned devices and public cloud services, different classes of data should, and should not, be held. Another step may well be required here to ensure users, including especially senior managers and business line executives, are not only aware of the policies but also understand why they exist.
Data discovery and classification may also identity opportunities to rationalise and consolidate the underlying storage infrastructure, as well as highlighting areas where the data protection and security solutions should be enhanced.
The business case for some of these steps, most notably the consolidation of storage platforms, can be quite straightforward to make. Equally there may also be a good case for making use of some form of active archive that can help minimise costs associated with primary storage growth.
Other activities may require that business stakeholders be made aware of some of the more value-oriented benefits deliverable through more effective data governance and information management. In economically tough times, however, this is likely to require clear articulation of the advantages better information access and improved decision making in the context of the customer’s business.
The bottom line is that data fragmentation is causing pain and concern out there, which presents a range of possible entry points into new business accounts, and a lot of cross-selling opportunity thereafter.
CLICK HERE TO VIEW ORIGINAL PUBLISHED ON

Registration required